Application Architecture
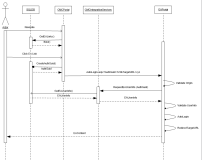
Users that have already authenticated within Portal, may access external application content via a seamless login methodology. The following sequence diagram depicts the interactions between the end user, Portal, the proposed integration web services, and the external application.
Sequence Diagram – End-to-End Simplification
This simplified diagram shows the interaction between Portal and the external application. When a user attempts to access external content, a time-to-live GUID is created in the Anthology Student database and is sent to the external application to use as a temporary access key into the web services. The external application must support a custom AutoLogin.aspx page and must process the GUID, TargetURL, and orchestrate communications with the integration web service.
The web service is consumed by the external application to request user specific information that facilitates identification of the user, and results in an automatic and seamless login to the external application. The user is then presented with access to external application content.
Security
Interaction with an external application raises several security concerns related to the exposure of confidential information. During the execution of the seamless login transaction, a time-to-live GUID is transferred from Portal to the external application. If not encrypted, the GUID could be intercepted by a third party and used to obtain access to the Integration web services and thereby access a user’s confidential information. The following steps should be considered to tighten the security model:
Requirements:
-
The external application should attempt to validate the source of the page request originating from Portal. All seamless login attempts should be limited to pages within Portal.
-
Integration web services should attempt to validate the source of the web service request. All requests should be limited to pages within the external application.